Are you confident that your company’s approach to cybersecurity is up to scratch? Do all your employees have secure video conferencing software at home that they’re using safely? Many companies’ security frameworks can barely be called that. They’ve been pieced together over time and on a “need-to-do” basis. Because of the time and money required to prepare for such events, even smaller organizations can experience consternation when faced with these changes. However, failing to adequately prepare for the changes could prove far more costly than spending the time and money necessary to make these preparations.
In this article, we will discuss 7 ways to build a security framework for your business.
What is a security framework and why is it necessary?
A security framework is the sum of policies and processes put in place to protect an organization from cybersecurity threats. You will no doubt have some components of this already in place, but there are bound to be areas left uncovered. This can leave your organization at risk of being attacked.
Additionally, having such a framework will help your organization be ready to face any cyberattacks, or better, avoid one. However, it’s okay if you don’t have a functional security framework in place. You are not alone.
A study discovered that only 49% of senior business executives think their organizations are equipped to identify a cybersecurity threat. If a threat is identified, then what happens? Don’t worry: Establishing an ideal security framework for your business is not as onerous a task as it may sound.
How do you go about building the ideal security framework for your business?
7 ways to build the ideal security framework
1. Identify your goals
The framework you require depends on the industry you’re in and the tools, networks, and systems you use on a day-to-day basis. For example, communication tools in the workplace vary widely from business to business. This makes a one-size-fits-all solution unrealistic. Additionally, sector legislation will differ from country to country; so will national legislation. Therefore, the solution must be bespoke to your requirements.
An example of this is the healthcare sector. If you handle personal health information in the US, you are obliged to follow HIPAA regulations regarding security. However, things are different if you operate in the UK where you would have to follow the NHS compliance approach, which often means implementing tools such as Cyber Essentials. It demonstrates how possibly the most important stage of building a security framework is to correctly identify your goals.
2. Conduct a thorough risk assessment
Conducting a thorough risk assessment of your organization’s approach to cybersecurity is the optimal way to identify the current areas that may pose a threat to it.
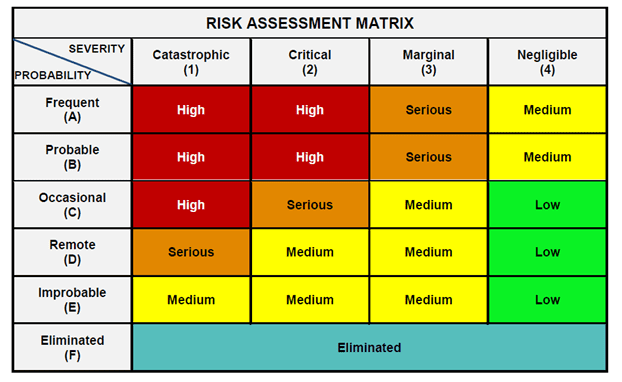
The risks identified in this assessment are the loopholes in your system, and they need addressing. Remember that risks can change over time. An honest and thorough risk assessment will go a long way to identifying your requirements and informing your overall approach going forward.
But what’s the greatest risk?
3. Watch out for people!
It is people, not things, that cause the greatest security risks.
Not all employees will apply the same diligent approach to cybersecurity as you do. A stringent set of policies and procedures will mitigate this to a great extent, but it’s always worth establishing internal protocols regarding who gets access to which information. For example, if you’re an SME and have grown quite rapidly in your early years, your processes may not have kept up with where your organization currently sits. Do all employees have access to all (or most) levels of information on your company database? If so, do they all need this?
It’s always worth making those with access to privileged information sign a non-disclosure agreement (NDA) to provide an extra layer of protection. This free NDA template can get you started.
Now that’s all taken care of, let’s look at some of the different security standards out there.
4. Adopt some security standards
As we discussed earlier in this post, the security framework you require depends on factors such as sector and location. Fortunately, there are a few standard solutions out there just waiting for you to adopt them. Here we’ve selected four of the main ones you’re likely to encounter:
- ISO 27000 family: The International Organization for Standardization (ISO) is undoubtedly the most globally well-known body concerned with information security. The ISO 27000 family of information security standards provide an exceptional basis for your security framework. ISO 27001 (information security management) and ISO 27701 (information privacy management) are probably the most useful—and certainly the most common—of the ISO 27000 family standards.
- NIST: The National Institute of Standards and Technology (NIST) offers a cybersecurity framework with best practices to help you secure your data and networks. This framework is incredibly comprehensive, but you can select the components you need, leaving the rest. This one is exceptionally useful for US companies wishing to secure a federal contract.
- CIS: The Center for Internet Security (CIS) provides an exceptional framework through which to keep your data and networks secure. CIS controls are growing increasingly popular globally, and it’s easy to see why. The CIS provides a streamlined and easy-to-follow set of controls that are particularly strong in remote working and cloud-based security, which, let’s face it, most organizations use these days.
- GDPR: The General Data Protection Regulation (GDPR) is an EU regulation that covers the handling of personal data. You’ll need to comply with this if you intend to do business in the EU. Find out if your website is GDPR compliant.
5. Prepare for breaches
Despite all your best intentions and preventive measures, breaches can still happen. A robust breach response system will mitigate against any intruders who do slip through the net. Essentially, it’s the second line of defense when your first one fails. It should cover every area, such as preparation, identification, containment, eradication, recovery, and, ultimately, lessons learned. When you have your system in place, all your staff should be made aware of your protocols and know exactly what to do after a data breach.
However, that doesn’t mean the work is done.
Your system will need to be frequently updated to ensure your response remains relevant and is sufficient to deal with any new threats that come along. And let’s face it, in the fast-moving cyber environment, new ones are coming along far too frequently
6. Secure your data
The next step is to adopt a stringent set of security measures, including encryption. As more data is stored on cloud-based systems, it is essential that this information is not an easy target for hackers.
Installing some powerful encryption software will not only protect your data from being a sitting duck for miscreants but will increase confidence among your clients that confidential, and potentially harmful, the material is being handled diligently.
It’s surprising how many organizations overlook this aspect of their security framework. A recent survey showed the extent of how little people trust the way their information is handled, with no industry reaching a trust rating of 50% for data protection. Therefore, robust encryption is not only required for your sensitive company information but also your wider reputation among your clients.
7. Keep a recovery plan
Despite your best efforts, your security can still be compromised. In recent years, organizations such as NASA and the FBI have been subject to security breaches that have led to the compromise of their data. Therefore, you should not think it can’t happen to you. It is therefore vital to have a stringent security disaster recovery plan in place.
A security disaster recovery plan should complement (but be separate from) your organization’s broader business continuity plan. It should allocate responsibilities and provide instructions to follow in case it all goes wrong. The plan should detail a comprehensive, multilayered approach that covers for all eventualities. It must be clear and straightforward to execute. After all, the plan will be worthless if no one understands it!
Once you have your plan, you should perform some company-wide drills so your people are prepared for any catastrophe that comes their way.
Time to start building your security framework
As we have discovered, the perils and pitfalls associated with building an ideal security framework for your business are plentiful. It is worth noting, though, that these things appear far more daunting than they are. It is just a case of diving in and pulling together all those parts so that you are cyber-secure.
The main takeaway from this post is the importance of identifying your organization’s goals, as this will help you choose the security framework that best fits your needs.
A holistic security framework that covers all aspects of your company can simplify your approach to security. Once implemented, you’ll find it easier to maintain than a hodgepodge of systems, standards, policies, and procedures. It’s easy to see how this could prove invaluable to both the long-term health of your business.
Author bio: Jenna Bunnell is a Senior Manager for Content Marketing at Dialpad. She is driven by and passionate about communicating a brand’s design sensibility and visualizing how content can be presented in creative and comprehensive ways. Jenna has also written for other domains, including Brightpearl and Dooly.
Disclaimer: This article is for general informational purposes only and should not be taken as legal or professional advice. The views and opinions expressed in this article are solely those of the author and do not necessarily reflect the views of our organization. We do not endorse any products or services mentioned in the article.







